Elcomsoft Wireless Security Auditor
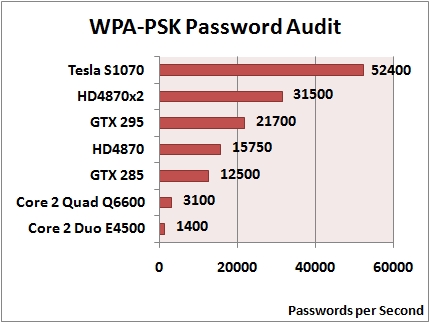
Audit security of your wireless networks and recover WPA/WPA2 passwords with Elcomsoft Wireless Security Auditor. In addition to the CPU-only mode, the new wireless password recovery tool features a patented GPU acceleration technology to speed up password recovery. Elcomsoft Wireless Security Auditor targets the human factor with smart attacks, combining dictionary attacks with an advanced variation facility. The tool accepts standard tcpdump logs supported by any Wi-Fi sniffer.
Elcomsoft Wireless Security Auditor official web page & downloads »