Today we have released Elcomsoft iPhone Password Breaker 1.20 which introduces two new features and fixes few minor issues.
Keychain Explorer
This feature allows to view contents of keychain included with encrypted device backup.
Mac users are probably familiar with concept of keychain — it is a centralized, system-wide storage where application can store information they consider sensitive. Typically, such information includes passwords, encryption keys and certificates, but in principle it can be anything. Data in keychain is cryptographically protected by OS and user password is required to access it. The closest Windows equivalent for keychain is probably Data Protection API.
iOS-based devices also have a keychain, but instead of user password, embedded cryptographic key is used to protect its contents. This key is unique to each device and so far there are no way to reliably extract it from the device.
Apple recommends iOS application developers to use keychain for storing passwords and other sensitive information, and one reason for this is that it never leaves device unencrypted. Here’s an excerpt from Keychain Service Programming Guide:
In iOS, an application always has access to its own keychain items and does not have access to any other application’s items. The system generates its own password for the keychain, and stores the key on the device in such a way that it is not accessible to any application. When a user backs up iPhone data, the keychain data is backed up but the secrets in the keychain remain encrypted in the backup. The keychain password is not included in the backup. Therefore, passwords and other secrets stored in the keychain on the iPhone cannot be used by someone who gains access to an iPhone backup. For this reason, it is important to use the keychain on iPhone to store passwords and other data (such as cookies) that can be used to log into secure web sites.
Prior to iOS 4 keychain was also included in the backup ‘”as is”, i.e. all data inside was encrypted using unique device key. This meant that it was not possible to restore keychain onto another device — it will try to decrypt data with key which is different from one used to encrypt data. Naturally, this will fail and all data in keychain will be lost.
To address this issue, Apple changed the way keychain backup works in iOS 4. Now, if you’re creating encrypted backup (i.e. you’ve set up a password to protect backup) then keychain data will be re-encrypted using encryption key derived from backup password and thus ca be restored on another device (provided backup password, of course). If you haven’t set backup password, then everything works like before iOS 4 — keychain encrypted on device key is included in the backup.
Elcomsoft iPhone Password Breaker now allows you to view contents of keychain from encrypted backup of devices running iOS 4. You will need to provide password, of course. Here’s screenshot of Keychain Explorer showing (some) contents of my iPhone’s keychain:
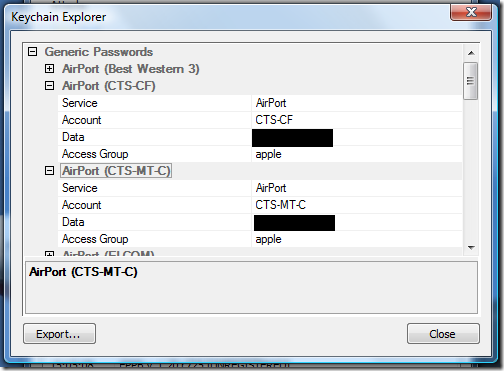
There are passwords for all Wi-Fi hotspots I have ever joined (and haven’t pushed “Forget this Network” button), for my email, Twitter, and WordPress accounts, as well as Safari saved passwords and even my Lufthansa frequent flyer number and password! 🙂 And I don’t use Facebook/LinkedIn/anything else on my phone — otherwise I guess credentials for those will be also included in the keychain.
Keychain Explorer will work only against backup which is encrypted. If you happen to have an iOS 4 device and want to get password from it — set a backup password in iTunes, backup device, use Keychain Explorer to view and/or export keychain passwords, and, finally, remove backup password in iTunes.
Password Cache
This feature is far less exciting than Keychain Explorer, but we believe it should improve user experience with Elcomsoft iPhone Password Breaker.
The idea is simple: all passwords which are found by EPPB or which are used to open backup in Keychain Explorer are stored in password cache. When you later try to open backup in Keychain Explorer or recover a backup password, program first checks password cache for correct password.
Passwords in cache are stored using secure encryption.
Also, there is a new EPPB FAQ online. Worth reading if you’re thinking of purchasing EPPB or want to learn more about it.
There is at least one really big update for EPPB coming in September or October, so stay tuned!



