Some time ago, I wrote a blog post on hacked Yahoo!, Dropbox and Battle.net accounts, and how this can start a chain reaction. Companies seem to begin recognizing the threat, and are starting to protect their customers with today’s cutting edge security: two-factor authentication.
A word on two-factor authentication. In Europe, banks and financial institutions have been doing this for decades. Clients needed to enter an extra piece of information from a trusted media in addition to their account credentials in order to authorize a transaction such as transferring money out of their account. For many years, bank used printed lists of numbered passcodes serving as Transaction Authentication Numbers (TAN). When attempting to transfer money out of your bank account, you would be asked to enter a passcode number X. If you did not come up with the right code, the transfer would not execute. There are alternatives to printed TAN’s such as single-use passwords sent via a text message to a trusted mobile number or interactive TANs generated with a trusted crypto token or a software app installed onto a trusted phone.
Online services such as Microsoft or Google implement two-factor authentication in a different manner, asking their customers to come up with a second piece of an ID when attempting to access their services from a new device. This is supposed to prevent anyone stealing your login and password information from gaining access to your account from devices other than your own, verified PC, phone or tablet.
The purpose of two-factor authentication is to prevent parties gaining unauthorized access to your account credentials from taking any real advantage. Passwords are way too easy to compromise. Social engineering, keyloggers, trojans, password re-use and other factors contribute to the number of accounts compromised every month. An extra step in the authorization process involving a trusted device makes hackers lives extremely tough.
At this very moment, two-step authentication is being implemented by major online service companies. Facebook, Google and Microsoft already have it. Twitter is ‘rolling out two-factor authentication too.
A recent story about a journalist’s Google, Twitter and Apple accounts compromised and abused seems to have Apple started on pushing its own implementation of two-factor authentication.
Two-Factor Authentication: The Apple Way
Apple’s way of doing things is… different. Let’s look at their implementation of two-factor authentication.
According to Apple, two-step verification is an optional security feature requiring Apple users to verify their identity via one of their trusted devices before they can do any of the following:
- Signing in to My Apple ID to manage their Apple account
- Making iTunes, App Store, or iBookstore purchases from a new device
- Receiving Apple ID-related support from Apple
Apple stipulates that “Turning on two-step verification reduces the possibility of someone accessing or making unauthorized changes to your account information at My Apple ID or making purchases using your account.” But is this implementation enough to secure personal information of Apple users? According to our research, Apple did a half-hearted job, still leaving ways for the intruder to access users’ personal information bypassing the (optionally enabled) two-factor authentication.
No Two-Factor Authentication for iOS Backups and iCloud Data
You can trade a little security for a bit of convenience. Then sacrifice some more security for some extra convenience. Then buy even more convenience at expense of security. There’s nothing particularly bad in this tradeoff in non-mission critical applications, but where should it stop? Apparently, Apple decided to maintain its image as being more of a “user-friendly” rather than “secure” company.
In its current implementation, Apple’s two-factor authentication does not prevent anyone from restoring an iOS backup onto a new (not trusted) device. In addition, and this is much more of an issue, Apple’s implementation does not apply to iCloud backups, allowing anyone and everyone knowing the user’s Apple ID and password to download and access information stored in the iCloud. This is easy to verify; simply log in to your iCloud account, and you’ll have full information to everything stored there without being requested any additional logon information.
In ElcomSoft’s opinion, this is just not the right way to do this from a security point of view. iCloud has been exploited in the past (see Norwegian Teenagers Hacking iCloud Accounts) and will be exploited in the future.
Geographic Restrictions
Even that half-hearted two-factor authentication scheme has not been rolled out globally as of yet. Initially, the two-step verification process was only available to Apple customers from the U.S., UK, Australia, Ireland, and New Zealand. Mexico, Germany Netherlands, Russia, Austria, Brazil, Belgium, Portugal, Italy and Poland were added to the list of supported countries later on; however, as of this writing, the feature was still not in fact available at least in Russia.
Playing Hacker
Let’s play hacker for a moment. Let’s say we have valid Apple ID and password information obtained by playing some dirty trick on a teenage girl. She has two-factor authentication enabled as you can see by logging into her Apple account at Apple – MyAppleID.
Clicking on “Manage your Apple ID” and entering her login and password, we can see that two-factor authentication is indeed enabled on that account:
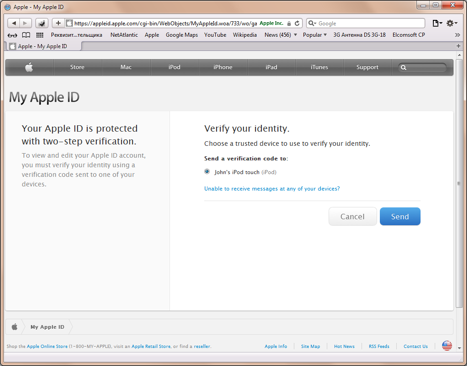
Apparently, if we want to initialize a new Apple device and start buying stuff from iTunes or Apple Store, we would have to receive a verification code on a trusted device:
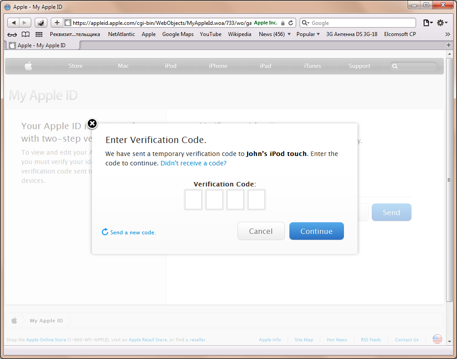
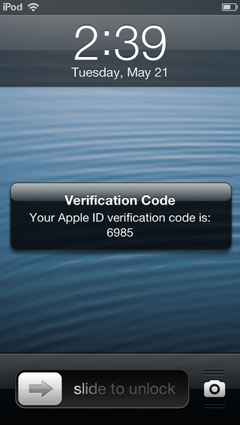
As you can see, the verification code is delivered right to the user’s lock screen via the Find My iPhone protocol (well, that’s not exactly a protocol, but an iCloud feature/service). This in itself is a concern, as anyone holding the device could read the verification code without having to enter the correct passcode.
You read it right: the verification code appears on the lock screen. This is not a text message, but rather a message delivered via the Find My iPhone – it’s the same way as if you lost your iPhone and used this service to send a notification to the current “owner” of the device asking to return it. Apparently, is the Find My iPhone service is disabled, the code is being sent as a text message (at least according to Apple Knowledge Base).
The reason for this, as we see it, is simple. Text messages will not work for iPod and iPad devices, but one of those could be the only Apple device you have. The Find My iPhone service will, however, work for either device.
Whatever the reasoning, the current implementation of two-factor authorization is clearly an afterthought. While the choice of the Find My iPhone service is understandable, Apple should have implemented a way to prevent certain types of messages from being displayed on the lock screen. Having something like “You have a new message. Please unlock your screen to see it.” would be nice.
However, regardless of two-step authentication settings, backups and documents are still accessible from anywhere. We can restore an offline or iCloud backup onto a new Apple device (or use Elcomsoft Phone Password Breaker to download and access on the computer) without being requested or entering the second passcode. Here’s how.
Using Elcomsoft Phone Password Breaker to Download Teenage Girl’s Private Photos from the iCloud
Yep, this can be done. We can access her iCloud backup even though two-factor authentication is enabled for that Apple account. Here’s how.
Use Elcomsoft Phone Password Breaker to sign into the iCloud account by using her logon credentials.
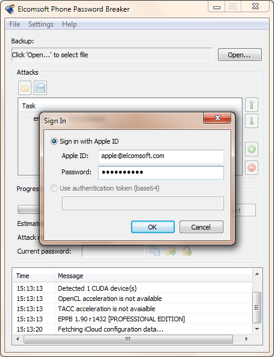
You’ll then select her Apple device from the list:
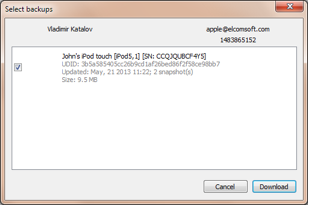
The information will be downloaded to your computer:
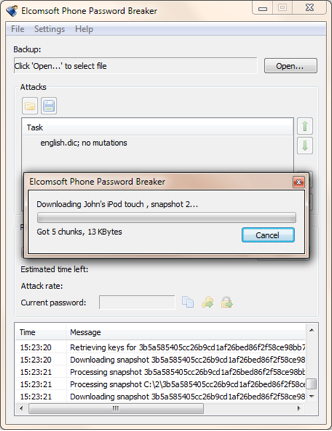
And you’ll get to see her personal stuff! All you need is some software that can browse and analyze offline iTunes backups, such as iBackupBot or more advanced Oxygen Forensic Suite, see Phone Password Breaker FAQ. For more information on iCloud backups, see iCloud backups inside out.
Here was the photo from the backup. Sorry, we decided not to publish it after all J
What about that teenage girl? Her private photos ended up in public access.
Using a Fresh iPhone to Restore Someone Else’s Backup from the iCloud
Now, what if we don’t want to bother with Elcomsoft Phone Password Breaker, and just want to restore everything from the iCloud onto a new device? In this case, all we need is still her login and password. No two-factor authentication kicks in during the process.
So let’s take a fresh phone and restore it from the iCloud (sorry for these low-res pictures; is not technically possible to make screenshots during the iPhone restoration process):
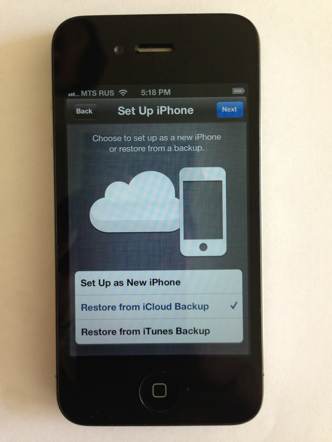
We’ll have to supply the correct Apple ID and password:
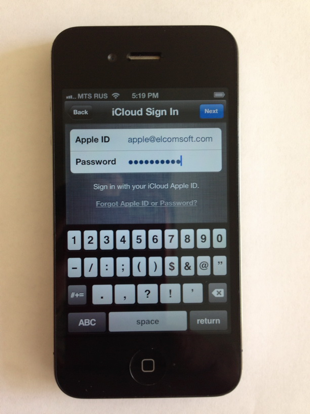
Agree with Apple’s terms of service and their Privacy Policy (let’s not make any jokes about it now):
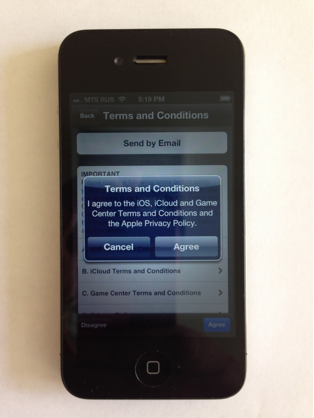
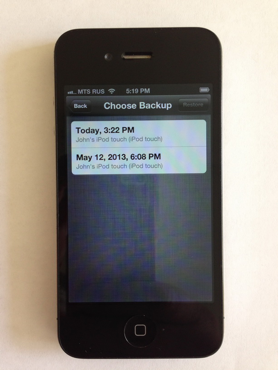
Choose the most recent backup:
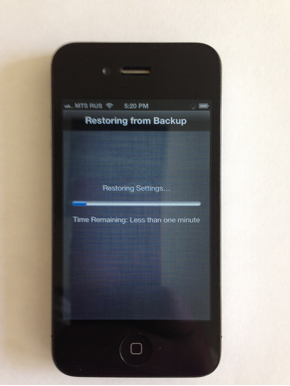
Wait a bit…
And make sure that everything has been restored correctly:
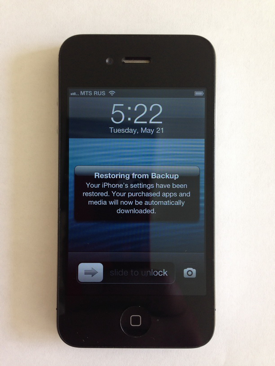
As you can see, nowhere in the process of restoring the new device from an iCloud backup was I asked for anything but Apple ID and the password. Ditto for Apple’s implementation of two-factor authentication.
One last thing to mention. After I restored a new, non-trusted device from the iCloud backup, I received an email from Apple:
Your Apple ID (xxx@xxxxxxx.com) was used to sign in to iCloud on an iPhone 4.
If you have not recently set up an iPhone with your Apple ID, then you should change your Apple ID password. Learn more.
While this is not related to two-factor authentication per se, this notification will at least let you know your information has been used to restore another device.
What about using Elcomsoft Phone Password Breaker? When I was using this product to download the backup instead of restoring it onto a new device, Apple did not send this email.
How Much Security Can We Trade for Convenience?
Apparently, Apple is torn between creating a secure environment and scaring away its customers by implementing security measures that are simply too tough.
iCloud access to documents is not yet integrated into two-way authentication process. As usual, Apple refuses to comment on anything concerning security, so we can only guess whether or not the two-step protection will be extended to cover information stored in the iCloud.
As we see it, there’s no big problem securing iCloud documents; a verification code can be delivered to iOS user via a text message or as a push notification via the Find My Phone protocol.
The situation with iCloud backups is more complex, and the solution is much less obvious. If legit customers are restoring their device from a backup, they normally have a valid reason such as initializing a brand-new device fresh from Apple store (Apple would certainly not want to scare them away), or restoring a device after a complete reset. Either way, at the time of the restore the device is not yet validated, so it’s not clear how exactly the pre-authorization step should be performed.
Conclusion
Is it a newly discovered security flaw? No, not really. Is Apple misguiding its customers? No: their two-step authentication process does exactly what they say it does. So what’s the deal?
For a record, I’d like to say that Apple’s approach in implementing two-factor authorization does not look like a finished product. It’s just not as secure as one would expect this solution to be. Don’t get me wrong; it’s not flawed or anything. It does everything that it claims to be doing (see above). What it doesn’t do, however, is protecting users’ personal information stored in the iCloud from unauthorized access. It’s not on the spec list, either.
In addition, the choice of the Find My iPhone service, while understandable, is clearly an afterthought, as supposedly secure verification codes are displayed in plain view on the lock screen. Finally, despite Apple’s claims, two-factor authorization is not currently available in all countries listed. We tried enabling two-factor authentication for an Apple account based in Russia, and found no way to do this.
Finally, two-factor authentication is not a silver bullet. There are scenarios where two-factor authentication simply is not enough. But still, it is a good idea to enable 2FA on all your accounts.
Updated on June 1, 2013: if the [trusted] device is locked with a passcode, then the verification code does NOT appear on the lock screen. Instead, you get the Unlock to view your verification code message, and have to enter the passcode to get it. Sorry that I missed it.














